
5 Ways to Secure The DevOps Workflow
The shift towards a DevOps-centric approach has been a transformation in the world of IT. DevOps pursues agile service delivery through lean practices, user-centric development, an emphasis on a collaborative culture, and enhanced coordination between development and operation teams.
However, with this scaling role, it’s time to evaluate the current security climate specifically for DevOps and the IT world to ensure a secure workflow. Here are five effective ways to enhance security while simultaneously promoting organization goals.
What DevOps Is and Why it’s Vital
DevOps integrates software development and information technology (IT) into a single team. This approach aims to facilitate faster software delivery by creating a continuous development loop of design, feedback, evaluation, and redesign.
Via an integration of automation of development pipelines, DevOps can create solutions and best practices to build, test, and deploy code. This marks a significant contrast from the waterfall approach, which separates project development and testing stages. If any delay occurs in this approach, it slows down the entire process.
DevOps pipelines are thus quicker, eliminate backlogs, and ensure effective communication throughout the entire process. The result is not only more rapid deployment but products that better fit user and developer needs.
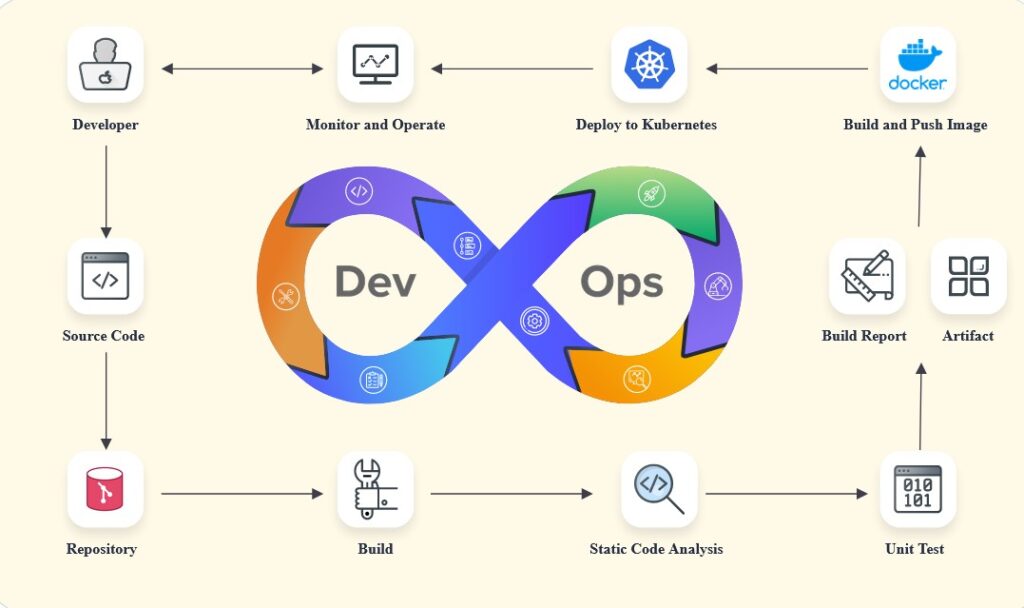
Securing DevOps Workflows
With any workflow, but particularly one so reliant upon communication as DevOps, there are numerous areas where vulnerabilities may occur. This can lead to an increased risk of a data breach, the leak of sensitive information, or other issues that can put the project and the firm as a whole at risk.
That’s why before embarking on a DevOps approach, it’s essential to take the time to integrate effective security technologies and protocols.
1. Enable a VPN at All Times
VPNs or virtual private networks have quickly become an essential component of business practices across all industries. In the last couple of years, VPN service providers have likewise created enterprise-grade versions of the software to handle the totality of business needs—namely, security and privacy.
According to NordVPN, in DevOps, VPNs are especially useful because of the frequent exchange of information over secure and unsecured networks. Overall, VPNs create an effective base layer of security and should always be enabled.
Furthermore, DevOps teams must also adopt the latest cybersecurity best tools and practices. This includes using antimalware and antivirus software, password managers, two-factor authentication, and other essential tools for secure development.

2. Embrace a DevSecOps Culture
It’s time we put the Sec (as in security) into DevOps. Security should be incorporated in all stages of the DevOps pipeline. This means creating a culture built around established industry security practices.
This radiates from the top down. The security team needs to adopt new skills and conduct training sessions for all staff to achieve DevSecOps.
Likewise, team members need to recognize and write codes that can work with APIs, automate security tasks, and flag potential risks. In short, security should be everywhere throughout the DevOps pipeline.
3. Enforce Rigorous Credential Controls
Access controls have long been part of the IT infrastructure, but DevOps needs to go several steps further. Security managers must ensure the control and access to different pipelines and environments in monitored and centralized.
Doing so requires the creation of transparent and collaborative ecosystems in which developers and all team members understand their access privileges and roles, respectively.

4. Evaluate the Security of Your Software Supply Chain
You’re only as secure as the software you use. One flaw in it can expose your entire operations. Since developers rely on open-source libraries, frameworks, and codes, this becomes especially valuable. These materials may provide increased speed and functionality, but it’s essential to keep an eye on their vulnerabilities.
The first step is promoting visibility through comprehensive guidelines and policies. Likewise, use container technologies to create sandboxed environments and isolate potential vulnerabilities.
Finally, advise developers to only use open source elements that they’ve vetted and had the latest security patches. If a component has had a weakness in the past, that’s not a deal-breaker as long as it’s been disclosed and fixed accordingly.
5. Encourage Automation
The DevOps process is fast. That’s what’s so great about it. By automating security tools and processes, you can further enhance your security operations’ scope and speed as well as the entire project.
Key areas to focus on include:
- Code analysis
- Vulnerability Discovery
- Configuration management
- Software accessories
- Access privilege
- Network monitoring
- Threat detection and removal
Automation not only simplifies vulnerability discovery but also creates a vital additional line of defense. Further, automation empowered developers, security, and other team members to focus on their roles, saving time, and reducing human error.

Bonus: Vulnerability Management
Sometimes it seems it’s not a matter of if a vulnerability will happen but when. That’s why your DevOps team needs a mechanism to detect, evaluate, scan, and remove/remediate vulnerabilities across the DevOps life cycle.
These tools effectively ensure that all code is secure before deployment. It’s a multi-pronged approach that includes attack simulation, penetration testing, and identifying potential weaknesses. Just as development is continuous, so should security analysis be running tests and applying patches when needed even after the software has been deployed.
The Secure DevOps Workflow
In the next few years, we’ll only see the role of DevOps continue to grow. It’s likely even outside industries will apply versions of the DevOps model to their approach because of how effective it is.
So, enjoy the best of what DevOps offers by creating a secure ecosystem from start to finish. The last and most crucial step to add to this process is to build an environment based on communication.
Whether it’s a coder, security analyst, or other team members, everyone should feel secure enough to discuss openly not only the project but irregularities and other concerns they may have. By taking this communication all the way, it will allow for the best DevOps practices to ensure your projects always thrive.