
VPN Services, or Everything You Need to Know About VPN
A VPNs allows remote users to connect to a private server from anywhere securely. For example, employees working on the road or working at home can use a VPN to connect to the office network from their laptops securely.
And large companies with offices that span multiple locations use VPNs to provide a secure and universal network for all office sites.
Commercial VPN services allow people to disguise their places or protect their transmissions to connect to the Internet through private servers.
To continue working with Vpntesting, we’ll talk about Internet traffic when you use your local network to access various services on the Internet, the source of your network resources in your local area network (LAN).
However, if you connect to any of VPN, and all your traffic goes through it, you will see the outside world as part of the local VPN network.
Also, your Internet Service Provider will see only one link: the one that is installed between you and the VPN service that you use, and, of course, it is entirely encrypted. It is why your ISP will not be able to see what you are doing on the VPN.

VPN target
VPNs can connect multiple sites over long distances, like a wide area network (WAN). Nonetheless, VPNs use to expand Intranets – large private networks – around the world and provide access to a broader user base.
such as universities, Educational institutions, use VPNs to connect campuses and students to university machines.
To provide a user with access to a private network, users must first authenticate using a unique identifier and password through a remote portal. Commercial VPN software often logs in a user automatically.
VPN sometimes use through browser software (VPN), which requires the user to log in. The software then displays the desktop or network files of the remote computer, which can access through a browser.
Other always VPN encrypts and routes all Internet traffic through the VPN service.
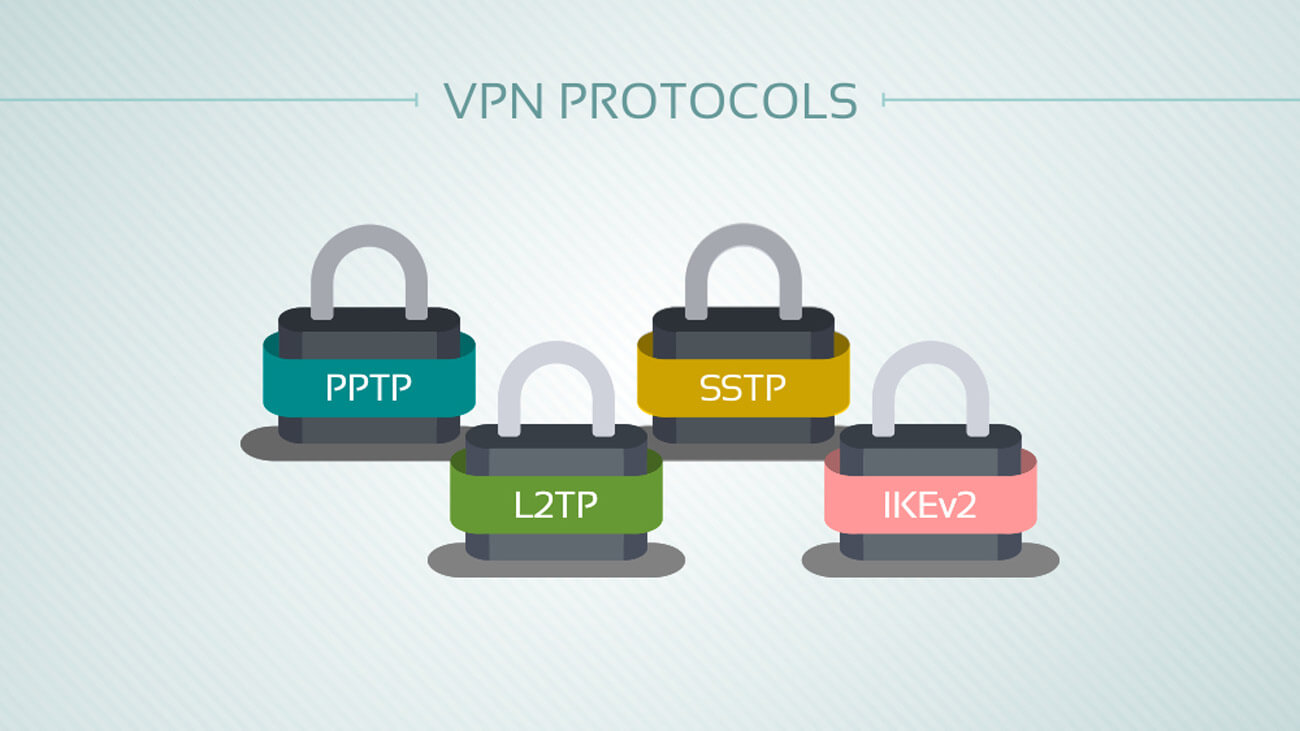
VPN Protocols
Due to the high secure nature of VPNs, they use several protocols that encrypt data traffic, which is especially important since data transmitted over a public network between two remote points.
The protocols used by VPN include IP Security (IPSec), Secure Sockets Layer (SSL), Transport Layer Security (TLS), Point-to-Point Tunneling Protocol (PPTP), and Layer 2 Tunneling Protocol (L2TP).
In both places, the “handshake” authentication method used. The connecting computer must be provided with a key that matches the required parameters for the receiving location to initiate this connection successfully.
VPN Benefits
Virtual private networks are traditionally a very inexpensive, cost-effective way to create a private network.
Using the Internet as a communication channel between sites is quite common, which reduces the cost of such services. VPNs are ideal for corporations in need of flexibility.
Why should you hide your IP address?
Your IP address is associated with all of your online activities. Your online activities can show your Internet searches, the sites you visit, the products you buy, and more. One way to hide your business on the Internet is to use IP masking.
Different categories of IP addresses include private, public, static, and dynamic. Most IP addresses assigned by ISPs are active, which means that a new IP address is assigned to your device every time you access the Internet.
However, dynamic does not mean private. Network activity can monitor by dynamic IP addresses.

IP masking hides your real IP address and location.
It makes it difficult to track or track your activities. IP masking performed using an encrypted VPN service, proxy server.
Note: Hiding an IP address is not the same as encryption. Unlike VPNs, proxies and do not offer encryption. Choose the right technology for your needs.
Hide your IP address using a VPN
Using a VPN (a virtual private network) is one of the best ways to block external objects from tracking IP addresses and monitoring online activities. It includes espionage by ISPs, search engines, websites, governments, hackers, and marketers.
A VPN masks IP addresses and sends Internet traffic through an encrypted VPN tunnel. If someone tries to browse or crack this data, he sees the VPN tunnel, and not what’s inside.
Also, the VPN can connect to servers from different countries to access websites and content with a geographical restriction.
To take advantage of the VPNs, you need a Vpntesting or service. Many VPN service providers offer a wide range of VPNs, tariff plans, and advanced features for a wide range of operating systems and mobile devices.

Mask your IP address using a proxy
Web proxies like hidester.com/en/proxy/ function as an intermediary between you and the Internet. When using a proxy server, Internet requests sent from the proxy server and information sent back from the proxy server.
In other words, this adds an extra leap to Internet requests, so it looks like they come from a proxy and not from your IP address.
Like a VPN, an anonymous proxy masks the true IP address and prevents devices from knowing where the traffic is coming from. Unlike any of VPN, a proxy does not encrypt Internet traffic.
Also, proxies protect only browser traffic, while a VPN replaces the local ISP routing for all services. Proxies are fast and easy to use, but if you need encryption, consider a VPN. You can read more about the best proxy servers here.
VPN disadvantages
Performance problems can be shared, often depending on the location of the remote client accessing the private network.
Data loss may occur due to the risk of transmitting data across multiple public networks.
To combat this, many VPN providers offer guaranteed Quality of Service (QoS) to ensure that there is no data loss during data transfer.
Also, Always keep in mind that some free Android apps can track users and infect their phones. You should be wary of free Android apps, and don’t forget to check user reviews before downloading free or paid apps.
However, he will not be able to conclude that it belongs to you directly, since the source of this traffic is a VPN server, not your computer.